A study conducted last year by cyber security vendor Bit9 revealed that more than a quarter apps on the Google Play store ask for permission to access information that isn't critical to their performance. Out of 400,000 apps analyzed, more than 100,000 of them were found to pose a potential security risk to their users. 72 percent of the 412,000 programs examined used at least one potentially risky permission - GPS location data, phone calls or numbers, information on contacts and such. For example, there was one wallpaper app in the analysis that asked for permission to access a phone's GPS data, when it was evident that the app didn’t need that information to function.
According to Bit9 CTO Harry Sverdlove, “The model for many of these applications is get as many permissions as you can get and then figure out what you're doing later”.
Whenever you download an app from Google Play you see an alert that explains the apps permissions – in other words, information that app will be able to access once you install it on your phone. But permission alerts are like EULAs – nobody reads them, a fact that developers take advantage of to include unreasonable permission requests knowing full well the user wouldn’t notice.
Even if a user were to read through the permissions, they might not gain enough insight to determine whether the requests are legitimate or not. An app can request permission to use network connection, for example, but you can be never sure what it's actually using that connection for. A social media app might use the network connection to download updates, but it might also use it to send your personal information to a remote server.
The best way to avoid falling into a trap is to read through the permission requests for all apps before you install them. Watch out for red flags such as requests to make calls or send SMS by apps that are clearly not made for communications, or permission to access GPS location when your location is irrelevant to the functioning of the app.
Yesterday, I wrote about an app that lets you filter apps on Google Play store by permissions. You should definitely add that app to your device – it will help you comb through the Play store when you start looking for new apps the next time. Being proactive is the only way to protect your privacy. But what about the dozens or so apps that you’ve already installed on your device without paying attention to the permission alert?
Permission Explorer
This is an easy to use app that lets you see how your installed applications can access your system. You can view apps by categories such as those that can access your localization, contacts, phone identity etc. You can also view them by detailed permissions such as which applications can access the vibrate function, or write to external storage, or wake lock. Figures within parenthesis indicate how many apps have access to that particular permission.

Permission Friendly Apps
Permission Friendly Apps allows you to go through your installed apps with a finely toothed comb. The app offers you a huge number of permissions filters. You can discover which apps can act as account authenticator, automatically start at boot, create Bluetooth connection, intercept outgoing calls, kill background processes, modify phone state, read Google settings etc. If you find an app that you think has gone too far with permissions, you can uninstall it right from within Permission Friendly Apps.

Permission Monitor Free
Rather than filtering the list of apps with a chosen permission filter, Permission Monitor Free automatically categorizes all apps based on the permissions they can access. Additionally, you can enable permission monitoring where the app will proactively check all new apps for the permissions you specify and alert you when an app asks for potentially risky permissions.

App Permission Watcher
If you are unsure which permissions are good and which are harmful, this is the app for you. App Permission Watcher includes a brief description of each permission with a small note describing the potential damage a malicious app could do if this permission is allowed. Harmful permissions are highlighted with red. App Permission Watcher also prepares a list of suspicious apps based on the permissions they have access to, although all of them looks pretty legitimate to me. On the other hand, some of the apps that I do consider risky were not marked as suspicious. So you may still have to use your own judgment.
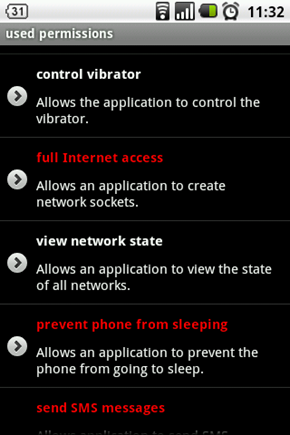
Photo credit: No trespassing by BigStockPhoto






Comments
Post a Comment